SSO Login Services
Once Devtron is installed, it has a built-in admin user with super-admin privileges having unrestricted access to all Devtron resources. We recommended to use this user only for initial and global configurations and then switch to local users or configure SSO-login.
Only users with super-admin privileges can configure the SSO. Devtron uses Dex for authenticating a user against the identity provider.
Below are the SSO providers which are available in Devtron. Select one of the SSO providers (e.g., GitHub) to configure SSO:
Dex implements connectors that target specific identity providers for each connector configuration. You must have a created account for the corresponding identity provider and registered an app for client key and secret.
Refer the following documents for more detail.
https://dexidp.io/docs/connectors/
https://dexidp.io/docs/connectors/google/
Create SSO Configuration
Make sure that you have a super admin access.
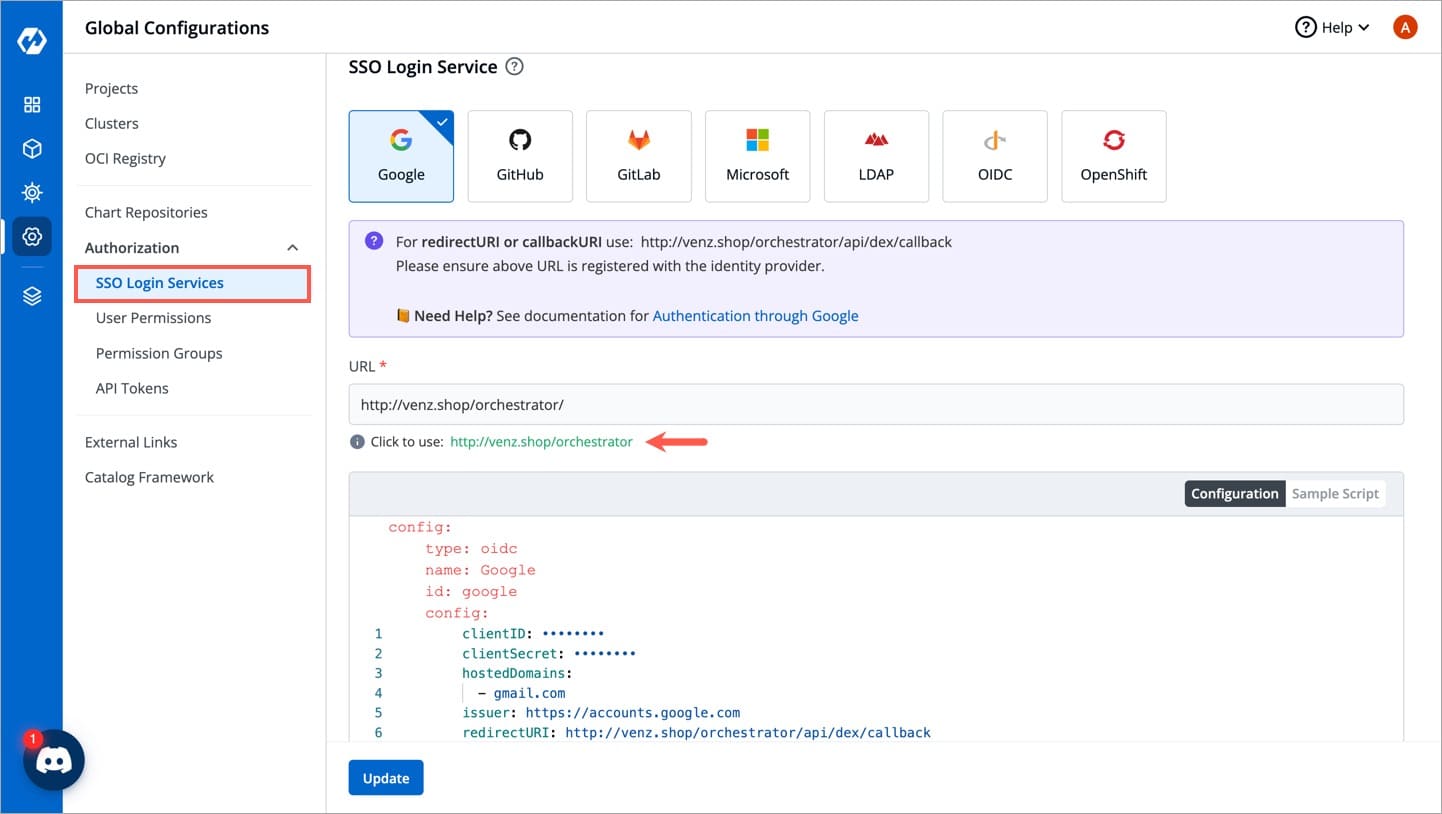
From the left sidebar, go to Global Configurations → Authorization → SSO Login Services
Click any
SSO Providerof your choice.In the
URLfield, enter the valid Devtron applicationURLwhere it is hosted.For providing
redirectURIorcallbackURIregistered with the SSO provider, you can either selectConfigurationorSample Script.Provide the
client IDandclient Secretof your SSO provider (e.g. If you selectGoogleas SSO provider, then you must enter$GOOGLE_CLIENT_IDand$GOOGLE_CLIENT_SECRETin theclient IDandclient Secretrespectively.)Select
Saveto create and activate SSO Login Service.
Note:
Only single SSO login configuration can be active at one time. Whenever you create or update any SSO configuration, it will be activated and used by Devtron and previous configurations will be deleted.
Except for the domain substring, URL and redirectURI remains same.
Update SSO Configuration
You can change SSO configuration anytime by updating the configuration and click Update. Note: In case of configuration change, all users will be logged out of Devtron and will have to login again.
Configuration Payload
type: Any platform name such as (Google, GitLab, GitHub etc.)name: Identity provider platform nameid: Identity provider platform which is a unique ID in string. (Refer to dexidp.ioconfig: User can put connector details for this key. Platforms may not have same structure but common configurations areclientID,clientSecret,redirectURI.hostedDomains: Domains authorized for SSO login (e.g. gmail.com, devtron.ai)
Next Steps
After configuring an SSO for authentication, you must add users in Devtron for them to be able to log in via SSO.
In case you have enabled auto-assign permissions in Microsoft or LDAP, relevant permission groups must also exist in Devtron for a successful login.
Last updated