Microsoft
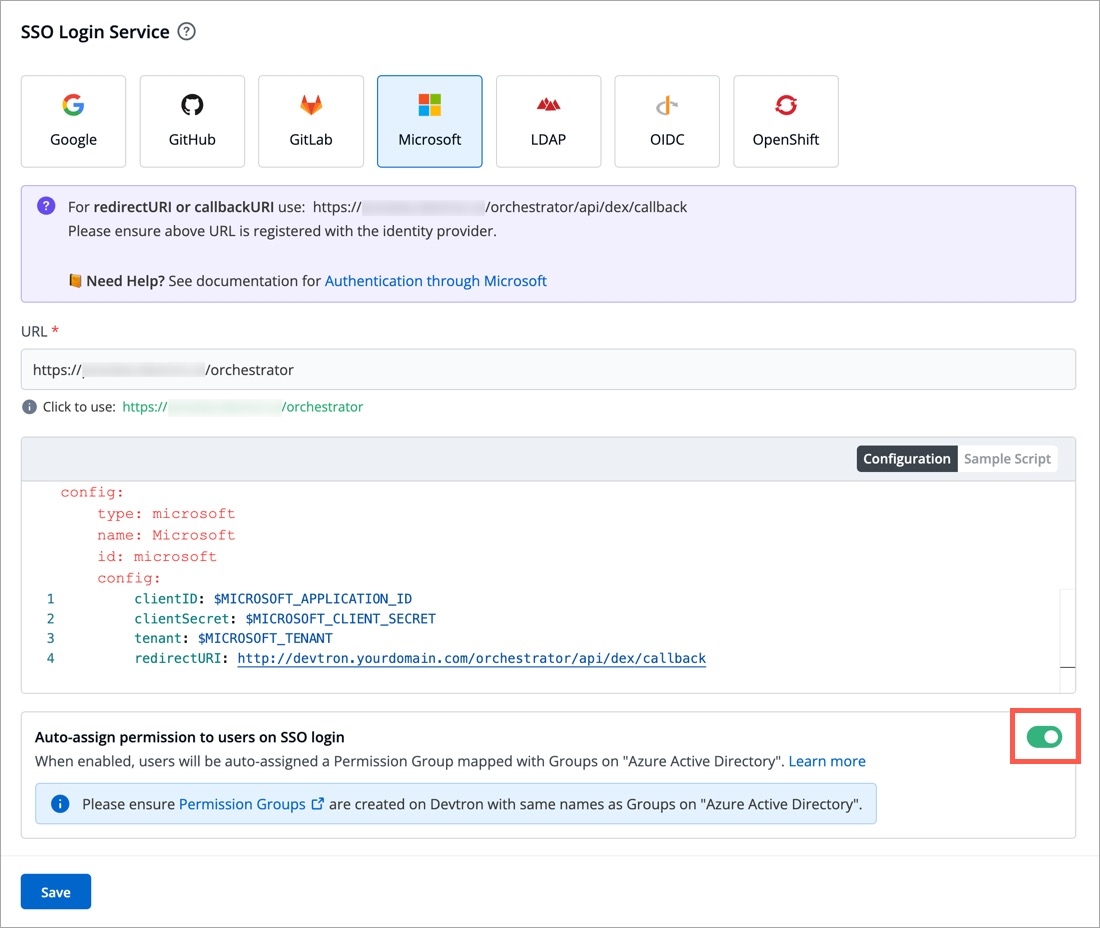
Sample Configuration
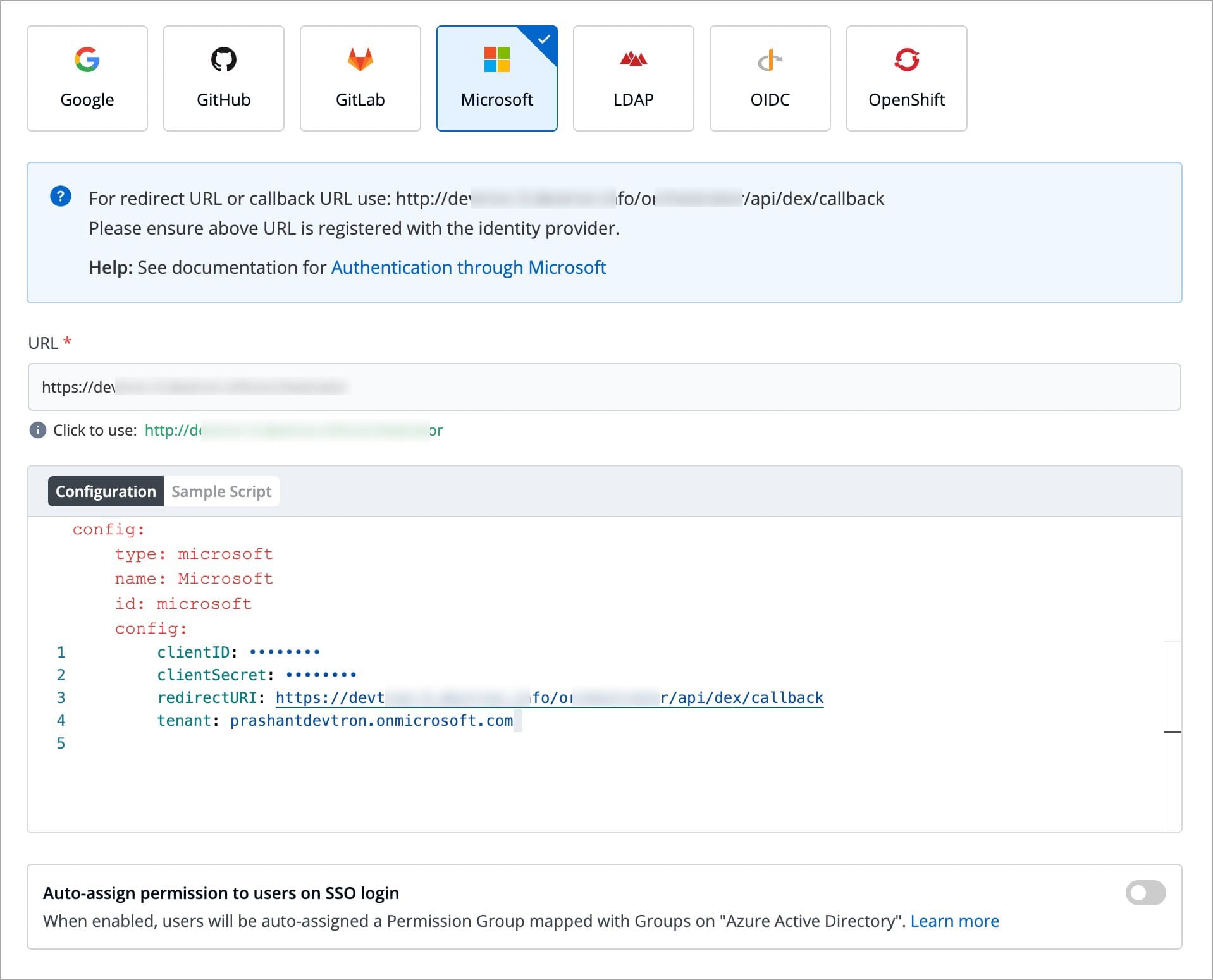
Values You Would Require at SSO Provider
Values to Fetch
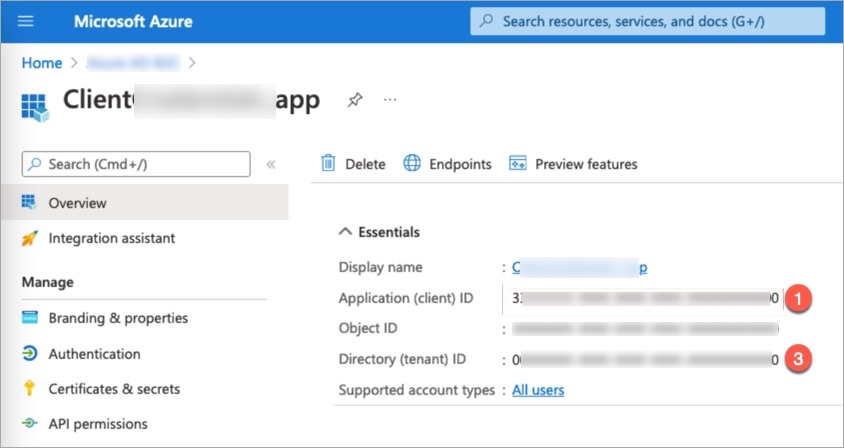
Fetching Client ID and Tenant ID 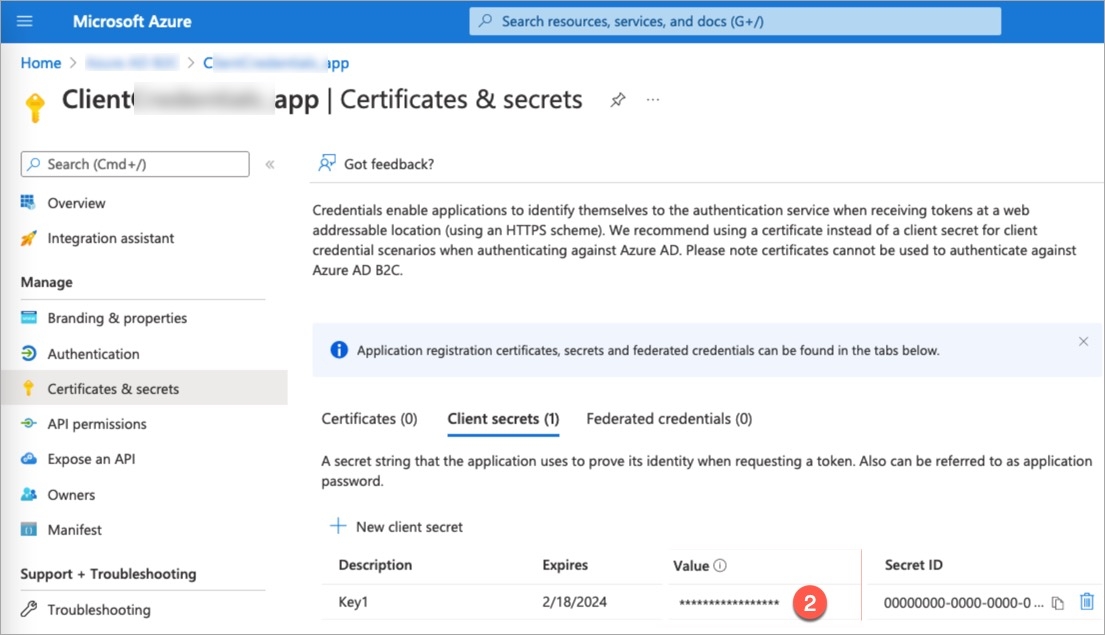
Fetching Secret
Values to Provide
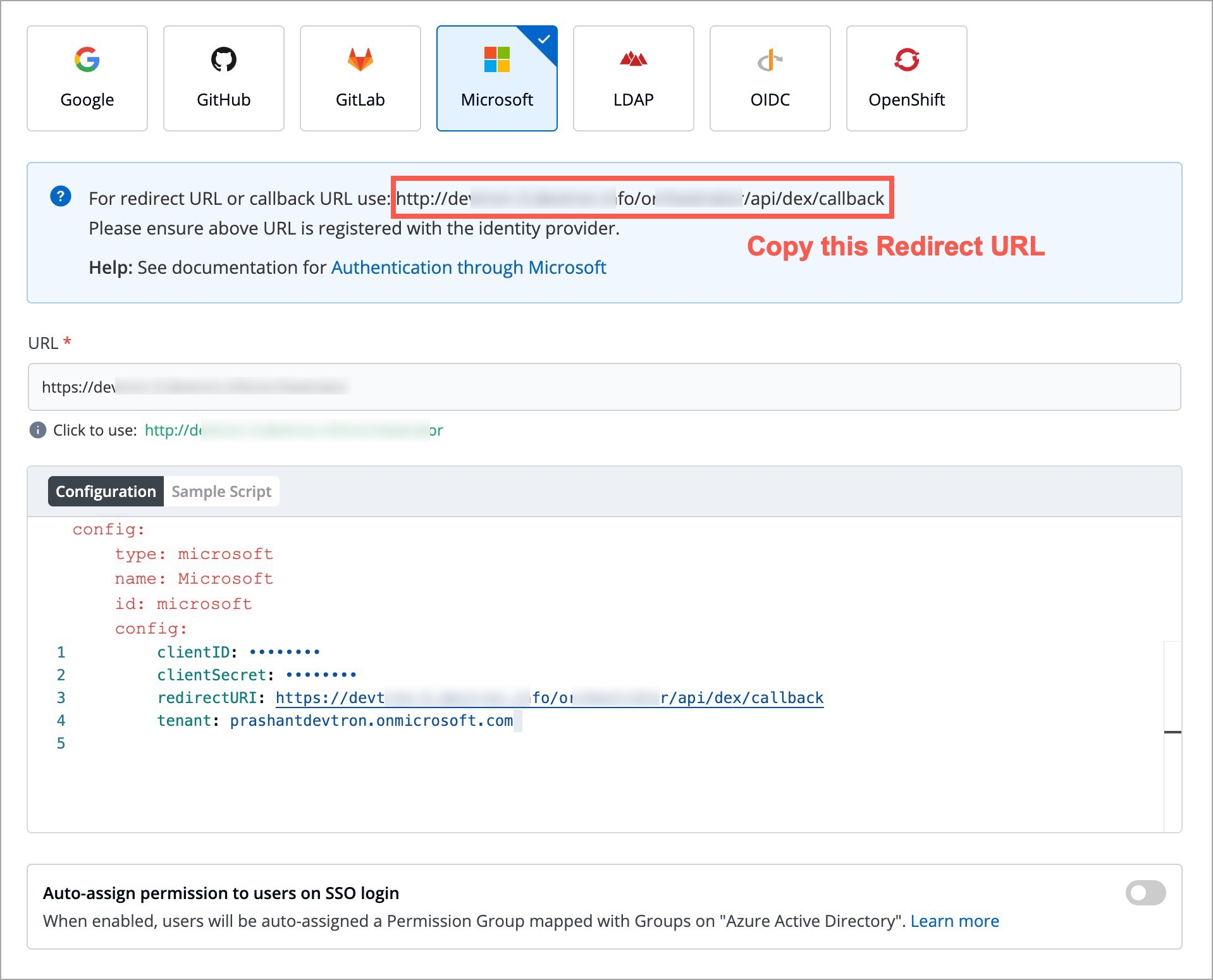
Copying Redirect URI from Devtron 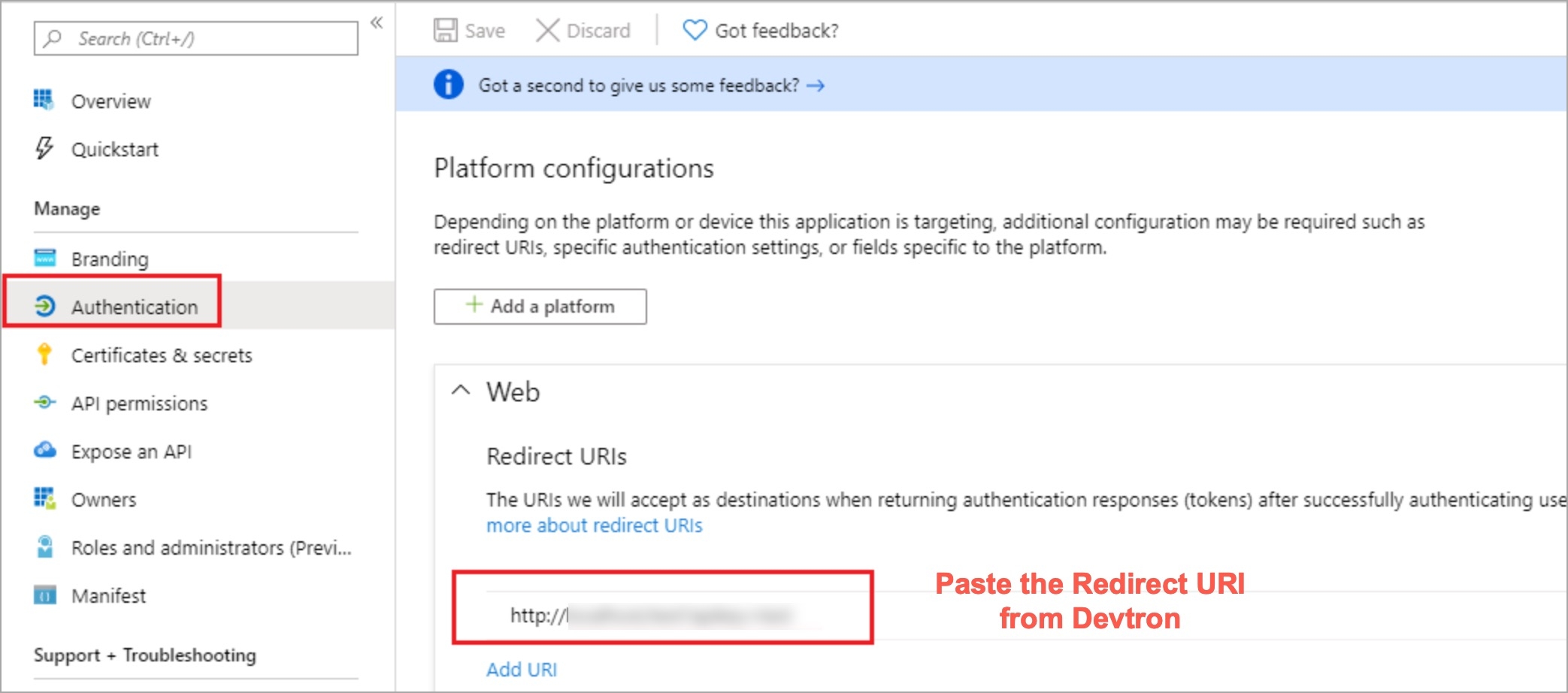
Pasting Redirect URI
Reference
Last updated
