Okta
Prerequisites
A verified account on Okta. Okta activates your account only if email verification is successful.
Here's a reference guide to set up your Okta org and application: Link
Tutorial
Steps on Okta Admin Console
Once your Okta org is set up, create an app integration on Okta to get a Client ID and Client Secret.
In the Admin Console, go to Applications → Applications.
Click Create App Integration.
Select OIDC - OpenID Connect as the Sign-in method.
OIDC stands for OpenID Connect. Click here to read more.
Select Web as the application type and click Next.
On the App Integration page:
Give a name to your application.
Select the Interaction Code and Refresh Token checkbox.
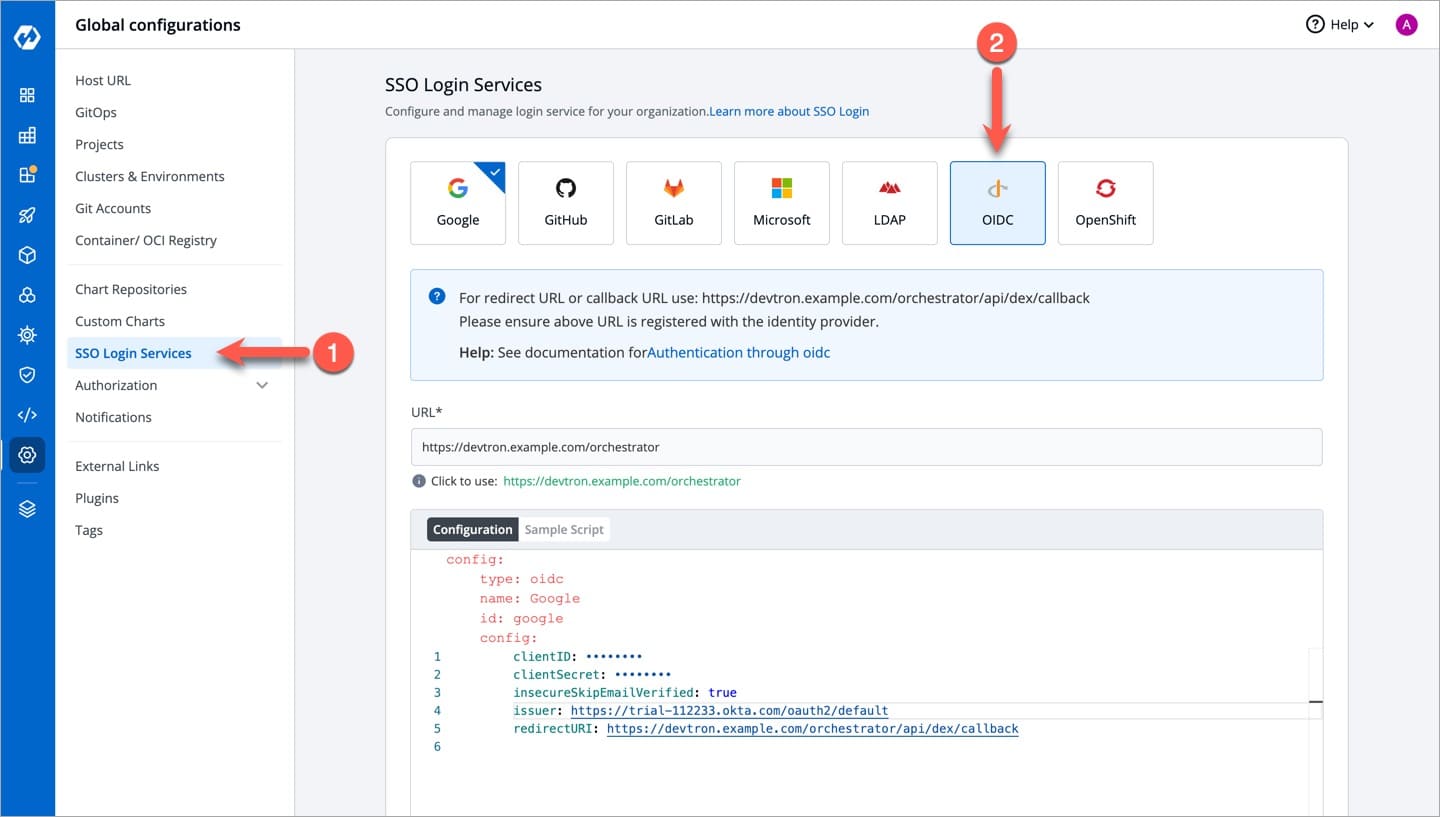
Now go to Devtron's Global Configurations → SSO Login Services → OIDC.
Copy the redirect URI given in the helper text (might look like: https://xxx.xxx.xxx/xxx/callback).
Return to the Okta screen, and remove the prefilled value in Sign-in redirect URIs.
Paste the copied URI in Sign-in redirect URIs.
Click Save.
On the General tab:
Note the Client ID value.
Click the Edit option.
In Client Authentication, choose Client Secret.
Click Save.
Click Generate new secret.
Note the Client Secret value.
Steps on Devtron
Go to the Global Configurations → SSO Login Services → OIDC.
In the URL field, enter the Devtron application URL (a valid https link) where it is hosted.
Under
Configurationtab, locate the config object, and provide theclientIDandclientSecretof the app integration you created on Okta.Add a key
insecureSkipEmailVerified: true. Note that this key is only required for Okta SSO. For other types of OIDC SSO, refer OIDC supported configurations.Provide
issuervalue ashttps://${yourOktaDomain}. Replace${yourOktaDomain}with your domain on Okta as shown in the video.For providing
redirectURIorcallbackURIregistered with the SSO provider, you can either selectConfigurationorSample Script. Note that the redirect URI is already given in the helper text (as seen in the previous section).Click Save to create and activate Okta SSO login.
Now your users will be able to log in to Devtron using the Okta authentication method. Note that existing signed-in users will be logged out and they have to log in again using their OIDC account.
Sample Configuration
Last updated